Everyday business documents continue to be one of the most significant sources of data loss. The US National Guard, Facebook, and WikiLeaks data leaks are prime examples of the damage these data leaks can cause. Even with the best security tools in place, users always seem to be able to find a way to circumvent security. Or, as in most cases, accidentally share data with the wrong audience, creating a serious security issue. Digital security watermarks provide a simple solution to warn users about a document’s sensitivity and intended audience to prevent mishaps. And, when all else fails, they can be extremely helpful in tracking the source of a data leak.
What is a Digital Watermark?
Watermarks have come a long way from rubber stamping or adding the words ‘confidential’ or ‘draft’ in grayscale across the top of a document via a word processor. Digital watermarks embed text or images inside digital content such as documents, images, slides, etc. Digital watermarking protects intellectual property from copyright infringement and helps prevent sensitive information from being shared with unauthorized parties or, worse, exfiltrated.
How do Digital Watermarks work?
Today’s digital watermarks embed important information into a document to track its point of origin, the handler and/or its owner for data security purposes. Details about the user, time/date of access, the machine it was accessed on, etc., can be embedded into a persistent digital watermark. These user-specific watermarks act as digital thumbprints that cannot be removed and travel with the document, making it easier to trace leaks.
What are the benefits of using Digital Watermarks?
Applying digital security watermarks to sensitive documents can help prevent data loss, misuse and unauthorized sharing in a variety of ways. They can be used to augment data security practices to:
- Dynamically apply critical information about the handler that cannot be removed by the user.
- Provide users with a visual reminder that they are handling sensitive information.
- Supplement user education and training relating to the safe handling of sensitive or proprietary information.
- Deter users from stealing documents or taking a picture of a document or image with their mobile device.
- Track a document’s chain of custody in the event of a leak.
- Provide read-only access by displaying the watermarked document in a secure reader that disables, print, copy, download and sharing capabilities.
What Types of Documents Should You Watermark?
Any document containing sensitive data you need to control or restrict access to is a good candidate for watermarking. Common types of documents you should consider watermarking include:
- Intellectual property (IP)
- Manufacturing plans
- Product specs and designs
- Images
- Financial documents
- M&A documents
- Human Resources (HR) documents
- Legal contracts
- Personally Identifiable Information (PII)
- Protected Healthcare Information (PHI)
- Federal Contract Information (FCI)
- Controlled Unclassified Information (CUI)
- Export Control Data (International Traffic in Arms Regulations (ITAR), Export Administration Regulations (EAR))
- Classified Information
15 Practical Uses for Digital Security Watermarks
The potential uses for watermarks are endless and can vary according to an organization’s individual needs, the type of data it manages, its industry and any associated regulatory requirements. Here are a few applications of digital security watermarks in enterprise and public sector scenarios.
Enterprise Use Cases
- Sharing previews of upcoming products with partners not meant for public distribution. For example, the release of a new toy or a script.
- Sharing and/or collaboration of IP and trade secrets with internal stakeholders and/or partners.
- Protecting images of products within documents and presentations.
- Protecting HR documents that contain PII, salary or disciplinary information.
- Protecting documents lying on a printer in a public space— think of all those unclaimed documents sitting on the public office printer.
- Sharing sensitive documents with third parties.
- Protecting images or information posted online.
- Clearly identifying that information has additional specific handling instructions, for example, “PROJECT X STAFF ONLY” or “UNCONTROLLED IF PRINTED.”
- Automatically applying relevant information such as the related industry, client, project or any other relevant document details.
- Applying disclaimers. For example, ‘Document intended for Client X only, any use outside this purpose is not authorized.’
- Marking the current document status (Working / Draft / Final / Approved / Released) and recent history / current version + timestamp of a document. For example, ‘This version is approved for public release by Person X.’
- Tracking the source of a leaked document – whether accidentally or deliberately shared with an unauthorized audience.
- Forensic tracking if a screenshot or photo of sensitive information is taken to track the leak source.
Government & Defense Use Cases
In addition to the use cases above, there are many specific use cases for Government, Defense and the Defense supply chain, including, but not limited to:
- Proper tagging of Freedom of Information Act (FOIA) Documents when the data is publicly released.
- Securely sharing tactical information for military units (such as OP Orders, travel documents, etc.).
- Multinational coalition and intelligence sharing.
- Properly tagging and labeling CUI, FCI, ITAR and EAR-controlled data in accordance with government marking requirements.
- Labeling and marking classified information according to government regulations.
Dynamic Digital Security Watermarks from archTIS
Manually applying watermarks is prone to human error. For example, if a user forgets the step entirely or marks the data wrong. They can also be easily removed if applied using a document editing app, making them insufficient for data security purposes.
What if you could ensure your sensitive documents were automatically watermarked properly and persistently?
archTIS solutions dynamically apply user-specific digital security watermarks that contain user, environmental and data attributes. They dynamically digitally stamp documents in their native application (e.g., Microsoft Word, Excel, PowerPoint, PDF) with a custom combination of attributes such as user name, IP address, date/time of access, document sensitivity level, intended audience, etc., according to simple, configurable rules to meet business requirements. archTIS watermarks are persistent. Therefore, users can share and edit watermarked document contents – but cannot edit or remove the watermark itself.
For further protection, watermarked documents can be displayed in the Secure Reader, an in-app viewer that provides read-only access, disabling functions such as print, edit, copy and save as. It ensures your most sensitive documents can’t be changed, downloaded or shared. You can also track access to the document via detailed audit logs.
archTIS’ Digital Security Watermarks can be dynamically applied to the following standard file types:
- Microsoft Office documents (.txt, .csv, .doc, .docx, .xls, .xlsx, .ppt, .pptx)
- Images (png, .jpg, .jpeg, .tif, .tiff, .bmp)
- CAD files (dgn, .dwf, .dwfx, .dwg, .dwt, .dxf, .ifc, .iges, .plt, .stl, .cff2)
- PDF documents
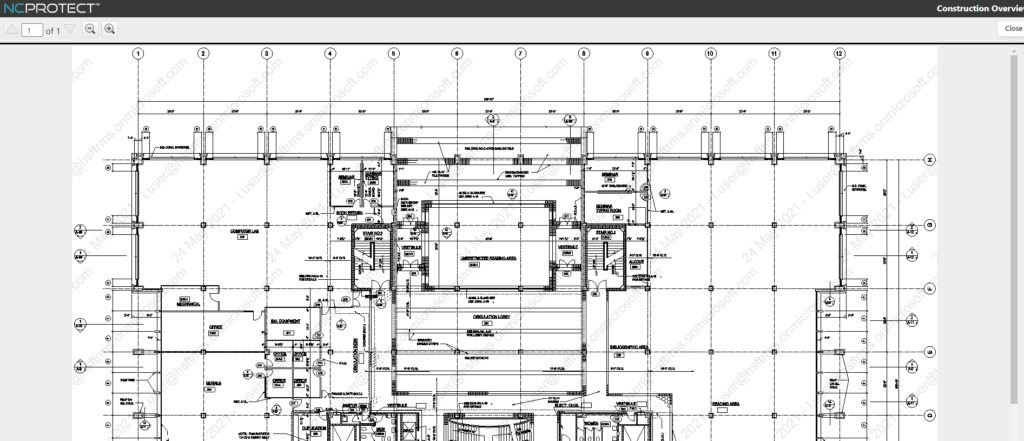
Above: With NC Protect and Kojensi, dynamically apply digital security watermarks and enforce read-only access to prevent copying, pasting, editing, or saving as capabilities.
archTIS can also apply multiple watermarks to a document. For example, watermark text and/or images in the document or only watermark an image within a document or slide.
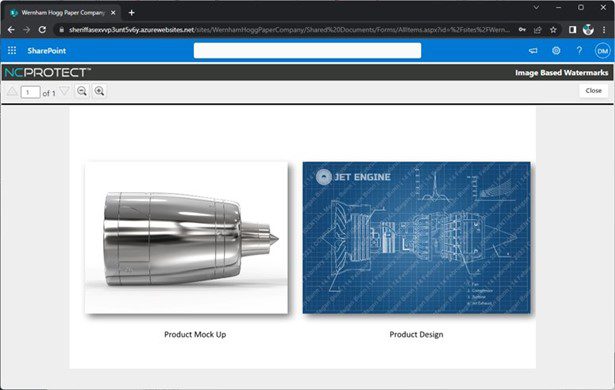
Above: Watermark individual images within a document with archTIS.
Want to Add Dynamic Watermarks to Your Security Toolbox? Contact Us.
Dynamic security watermarks add an essential layer of protection to safeguard sensitive information and regulated data and avoid compliance issues. If you could benefit from watermarking sensitive information in your Microsoft 365 collaboration applications or need a document management platform to securely share classified information, contact us today.


