TRUSTED Data Integration

Simplify the complexity of Structured Data Integration and Security at Scale
Designed for Defence & Supply Chain Data Integration & Security needs
Leveraging our deep expertise in policy-enforced ABAC and unstructured data protection, archTIS Trusted Data Integration (TDI) expands our product stack to offer a solution for integrating, visualizing and securing structured data at scale. TDI is designed to enable secure data fabric enabled Defence and supply chain data services. It solves these challenges with agility to meet business needs and enable customers to maintain a competitive edge.
Key Capabilities
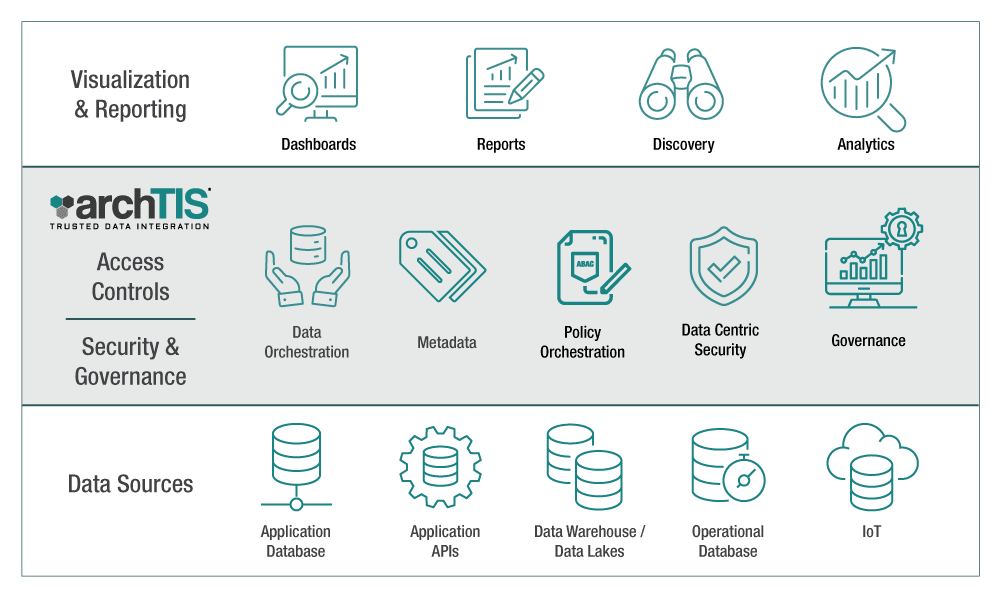
archTIS Trusted Data Integration (TDI) is a lightweight, fast and agile solution to solve the problem of how to integrate, secure and govern sensitive and classified structured data at scale and speed.
Leverage federated identity data for access decisions – same data, different identity, different view.
Orchestrate data in real time from multiple sources and formats.
Centrally author and apply access control and data protection policies to enforce security and compliance across data with minimal user impact.
Enable seamless data collaboration with multiple third parties.
Manage IP, Export Control, and ITAR data based on ‘need to know’ and ‘need to share’ principles.
Enhance data to support better access decisions.
Develop and publish self-serviceable data securely.
Provides comprehensive audit logs with built-in compliance observability and reporting.
TDI Simplifies the Complexity of Data Integration & Security at Scale
TDI’s policy authoring engine and workflow ‘blocks’ make it easy to securely display data based on the user and provide reporting for compliance. It provides centralised security policy orchestration and enforcement using attributes-based access control (ABAC) to ensure data is secure and governed.
Why archTIS Trusted Data Integration?

Enables Policy-enforced ABAC Security
- Enforces ‘need to know’ and ‘need to share’ principles across data.
- Adds Zero Trust Data Centric Security capabilities to data access.
- Add policy-based access control to legacy systems.

Simplifies Data Integration & Security
- Ingest and control access to data from multiple authoritative data sources.
- No specialised tech or compliance skills necessary.
- No interference with other services; wraps security around them.
- Goes from microscale to hyperscale quickly and cost-effectively providing consistency from edge to core.

Accelerates Outcomes
- Orchestrates security, governance, compliance administration and control.
- Enables speed of relevance for decision-making on data.
- Augments data to achieve high-quality security and compliance comes.
- Enables the balancing of existing constraints with security and productivity benefits.
