Blog
Stay up to date on industry trends, security advice, product news and more.

Safeguarding Classified Information: How to Prevent Insider Data Breaches
The US military's recent classified information breach has brought to light a significant concern within the security industry known as insider threats. Learn about strategies to prevent them.

How to Identify and Protect Personal Information
Handling personal information and PII can be a daunting task for businesses. Learn how to identify and protect personal information in enterprise collaboration systems.

What is Sensitive Data? Sensitive Data Definitions, Types & Examples
Data security and data breaches are recurring topics in the IT world. While it’s vital to keep all data safe from exploitation, it’s even more vital to keep the so-called “sensitive data” safe from exposure. This discourse would expose you to the definition of sensitive data, what makes data sensitive, and how to protect information from exposure, and exploitation.
Understanding the Proposed FAR CUI Rule
Examining the proposed FAR CUI requirements and what they mean for federal contractors when the rule becomes final.

15 Ways to Protect Data with Digital Security Watermarks
Learn how today’s security watermarks act as a digital thumbprint that travels with the document to prevent data loss and misuse.

Happy Holidays from archTIS
From all of us at archTIS Happy Holidays!

Understanding the Implications of the New Australian Cyber Security Act for Your Organisation
How the new Australian Cyber Security Act will impact your organisation, plus 3 steps to ensure compliance.

What is Data-centric Security?
A data-centric security strategy shifts the approach from a company’s outer defences to making the data itself more secure.

Join archTIS at MilCIS 2024
We are excited to share that archTIS will present two sessions, and our solutions will be featured in select partner booths at MilCIS 2024 from the 12 -14 of November.

9 Ways Data Vampires Are Bleeding Your Sensitive Information
Beware! Remote work and collaboration tools make accessing and sharing data easier than ever, leaving sensitive information at risk from data vampires...

Ensuring Classified Data Doesn’t End Up Public Using Data-centric Zero Trust
Classified data leaks have serious repercussions. Explore how data-centric zero trust can effectively thwart insider threats to protect classified data.
Tips for Managing Unstructured Data Security
Explore the unstructured data security and protection controls needed to ensure only the right users have access to the right content at the right time.

Understanding EAR Compliance Regulations: Tips for US and non-US Companies
Understanding EAR Compliance: Tips for US and non-US Companies to manage compliance and data security obligations
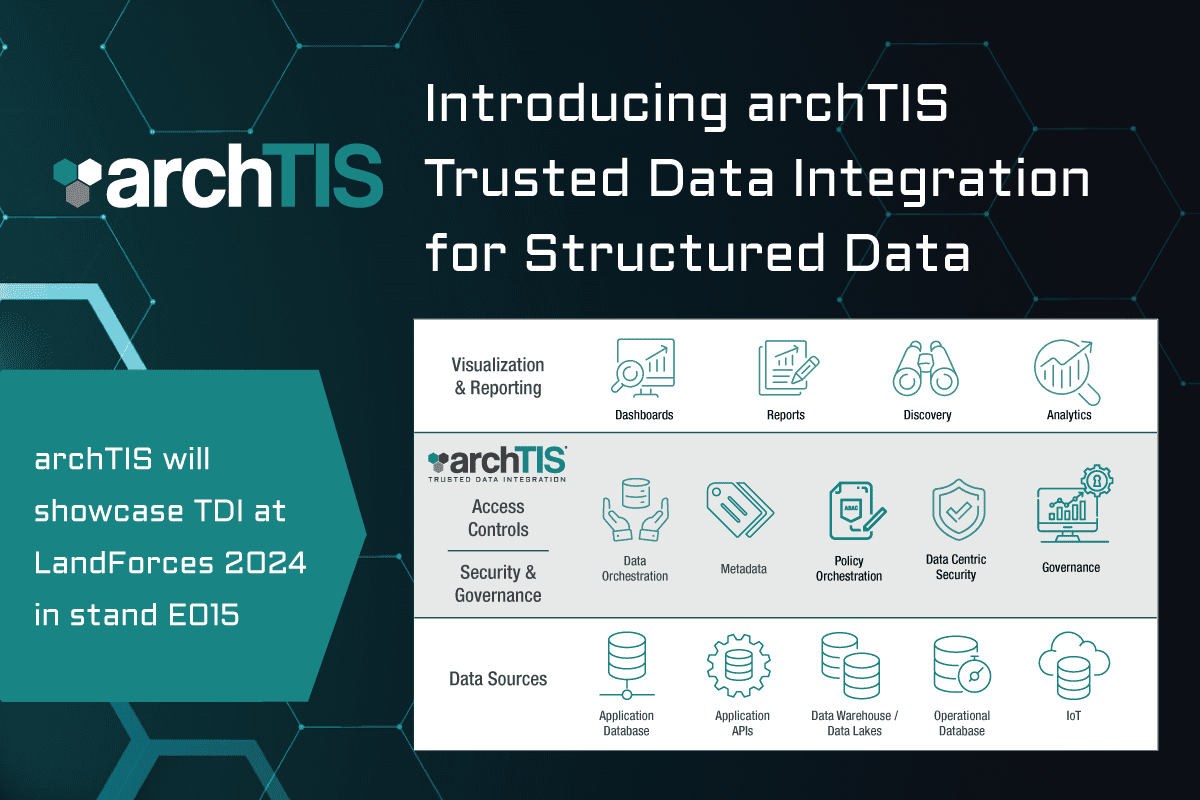
New archTIS Trusted Data Integration Solution for Structured Data
This week, during LandForces 2024 archTIS announced the launch of archTIS Trusted Data Integration, a new ...

Creating a Secure Community of Interest (COI) for Defence & Industry Information Exchange
Explore the use cases, challenges and tools for creating a Community of Interest (COI) for secure information exchange.

Understanding the Differences Between Fine-Grained vs Coarse-Grained Access Control
Fine-grained vs coarse-grained access control: How to choose the best option for your data protection needs.
Defense Supply Chain Data Security
This blog examines the top threats, best practices and tools for securing defense supply chain data security.

Why Artificial Intelligence (AI) Is Neither
What exactly is AI, and more importantly, how does it work? This blog delves into separating the facts from the hype.
No results found.
