Cybersecurity has become an important topic for the defense supply chain. The ever-increasing number of digital channels that data can be exchanged through, has exponentially increased the risk of data breaches and leaks. This puts a lot of pressure on these organizations to ensure that the risks associated with the handling of sensitive data are as low as possible. To help mitigate those risks, the US Department of Defense (DoD) suppliers and contractors must adhere to a number of regulations, including DFARS to ensure the security of information shared and collaborated on.
What is DFARS?
Defense Federal Acquisition Regulation Supplement or DFARS is a standard that is crucial for any defense supplier or contractor that works with the DoD. It applies to purchases and contracts for DoD contracting activities made in support of foreign military sales or North Atlantic Treaty Organization cooperative projects. Failure to comply with this, and other standards, would result in immediate contract elimination.
DFARS was created to mitigate potential risks of CUI leakage. Controlled Unclassified Information or CUI is a category of unclassified information that requires safeguarding or dissemination controls pursuant to and consistent with applicable law, regulations, and government-wide policies but is not considered classified.
The bulk of DFARS covers how CUI must be handled by each and every DOD contractor as specified in NIST 800-171. All contractors and subcontractors processing, storing, or transmitting CUI must meet the minimum security standards specified in the DFARS. Failing to do so can result in the loss of DoD contracts.
The DFARS rule set maps to NIST 800-171, as do other regulations such as CMMC, and covers 14 different categories, each having its own compliance ruleset. There are separate categories for Risk Assessment, Access Control, Maintenance, Configuration Management, and more. DFARS is over seventy pages long, which makes compliance a massive undertaking for any company that starts investigating this topic.
DFARS Compliance in Microsoft Applications
Microsoft has been making great strides to make its platforms compliant with various regulations, including DFARS, to support government, Defense and Defense Industry clients. It’s important to understand the different Microsoft product offerings to support the increased levels of security necessary for these entities:
| Platform | Availability | DFARS 252.204-7012 Compliant |
| Microsoft 365 Commercial | The public version of M365 that is available all over the world and is referred to most of the time when describing M365 as a service. Does not support DFARS 252.204-7012 compliance | No |
| Microsoft 365 Government Community Cloud (GCC) | The GCC version of M365 is available for local, state, and federal government, as well as recognized tribal governments. | Yes |
| Microsoft 365 Government Community Cloud (GCC) High | A relatively new M365 environment that is compliant to level 4 DOD security guidelines. Is only available to government contractors, federal agencies and the DIBs (defense industrial bases). | Yes |
| Office 365 DOD | Has the highest security level to date and is designed with DOD level 5 security guidelines. Can only be used exclusively by the DOD. | Yes |
Unfortunately, Microsoft 365 Commercial is not DFARS-compliant since it cannot support the process that is described in DFARS 252-204-7012 sections c to g. These sections describe the exact process the contractor must follow in case of a cyber incident, including everything from discovering the issue to preserving the logs and providing additional info for the damage assessment and forensic analysis. When it comes to meeting DFARS compliance, it is Microsoft’s official recommendation to migrate to Microsoft 365 GCC High in order to be compliant to each and every part of DFARS.
However, moving to GCC High can be a problem for contractors, especially SMEs. First of all, the price jump from Commercial to GCC High is rather significant and may not be suitable for smaller contractors/suppliers purely for monetary reasons.
At the same time, there are additional fees to be considered, such as consulting, migration, and so on. There is also the time factor to be considered – since the entirety of a company’s platform has to migrate from Office 365 Commercial to GCC High, the process itself takes multiple months, often taking more than half of a year to complete the process.
How CMMC Fits Into the Process
A company should evaluate whether or not migrating to GCC High is right for them. To do this we need to look at another set of guidelines that apply to Defense contractors – the Cybersecurity Maturity Model Compliance (CMMC). The CMMC framework was created to make it easier to perform the assessment process when it comes to the contractors and suppliers in the US Defense Industrial Base (DIB). It has three different levels as detailed in the chart below.
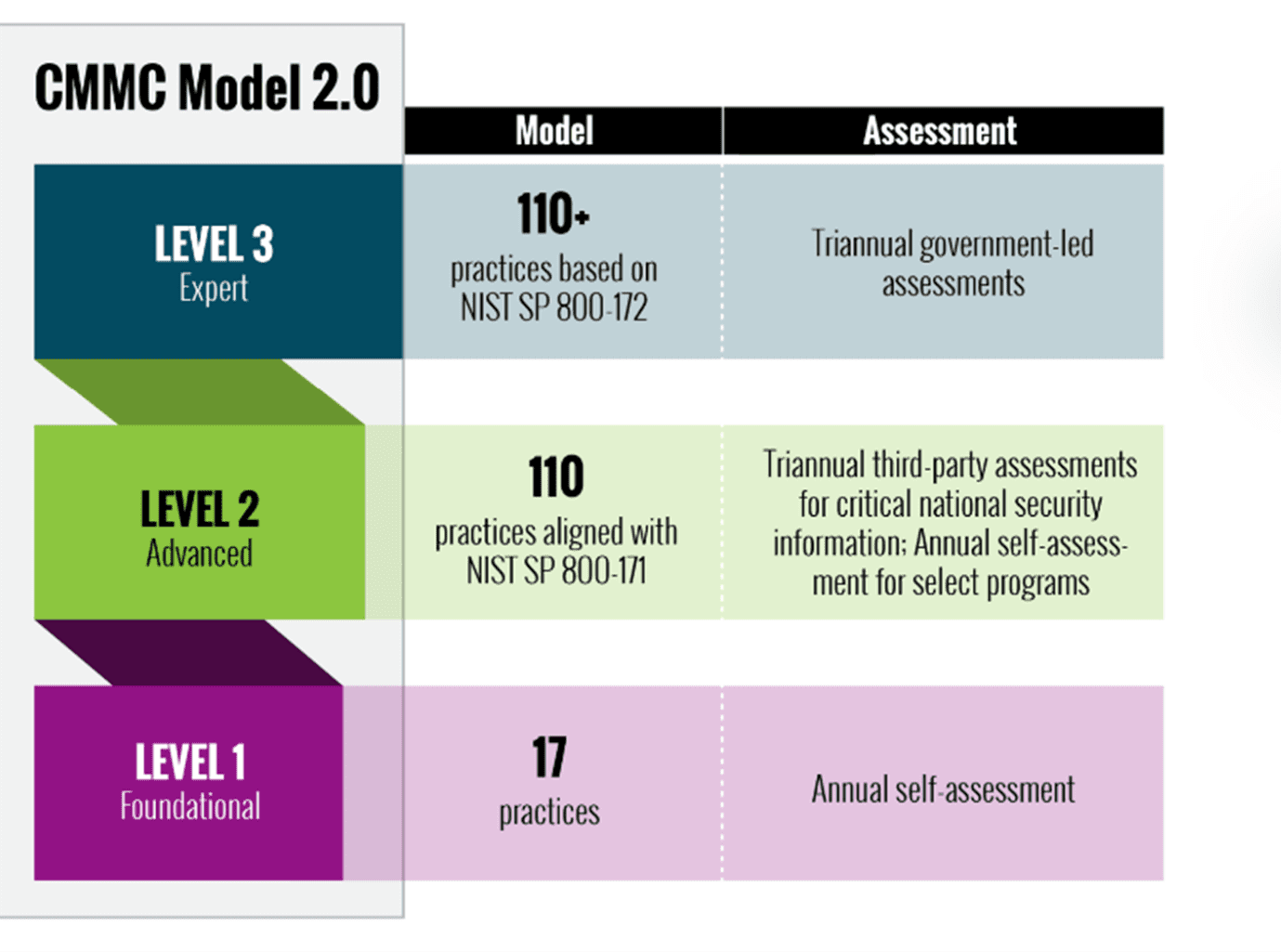
Not every single company that works with the DoD needs to meet Level 3 compliance. In fact, a lot of the companies are only required to meet Levels 1 or 2. However, if the goal of the company is to pursue higher-level government contracts in the near future, then they would have to become Level 3 compliant.
Choosing a GCC environment to meet Level 1 or Level 2 CMMC standards might be the better way to handle compliance as a whole. This is possible because GCC on its own serves as a middle ground of sorts between the Commercial and the GCC High environments in terms of feature parity and migration costs.
That is not to say that GCC is a definitive solution to all problems with Microsoft 365 DFARS compliance for contractors. Generally speaking, choosing GCC as the main environment effectively limits the company’s capabilities for the foreseeable future. Additionally, GCC suffers from the same problem that GCC High has, albeit not at the same degree. This problem is feature parity – there are still some features that have not been introduced to GCC that are available in the Commercial version.
The topic of migration as a whole also has to be considered with a lot of planning and calculation in mind. It is a long and often complicated process that could easily take months of the company’s normal working time.
Third Party Solutions to Aid in DFARS Compliance
Third party solutions can aid in meeting DFARS, CMMC, NIST and ITAR information security requirements for CUI – no matter what Microsoft platform you’re running.
NC Protect enhances native security capabilities to empower secure collaboration within and between defense and supply chain partners using attribute based access control and protection policies to dynamically:
- Scan and tag data or leverage Microsoft Purview Information Protection (MIP) sensitivity labels in combination with other file and user attributes to dynamically adjust access and data protection.
- Control what users can see, how they can use and share information and with whom at the file, message and chat level using granular Attributed-Based Access and Sharing Control (ABAC) e.g., security classification and nationality.
- Get unique security capabilities to enforce secure read-only access, hide sensitive files from unauthorized users, apply dynamic personalized watermarks and alert on unauthorized access or internal data spills.
- Embed CUI Designator Label information including Owner Name, Controlled By, Category, Distribution/Limited Dissemination Control and POC into documents, including CAD files, as a watermark.
- Remove/redact sensitive or confidential information, such as keywords or phrases, in a document when viewed in its native application (Word, Excel, PowerPoint and PDF) or when the file is presented in the NC Protect secure reader for legal or security purposes.
- Integrate user activity and protection logs with Microsoft Sentinel for further analysis and downstream actions.
Extending a Zero Trust approach used for system and application access to file access and sharing with NC Protect helps ensures compliance with DFARS CUI handling requirements, as well as a number of domestic and international information security requirements.
Conclusion
DFARS compliance is complicated. It requires a lot of research and evaluation of a company’s current and future goals to figure out what type of Microsoft 365 environment makes sense for them. Between the security features built-into Microsoft platforms and the added capabilities that NC Protect brings to the table Defense and supply chain organizations can feel confident that the information stored, collaborated on and shared via M365 applications is secure and meets DFAR compliance guidelines for CUI.


