Discovering and Protecting Sensitive Data Using Existing Classifications and Metadata
With the introduction of various compliance requirements such as HIPAA, PCI and GDPR (to name a few from around the world), there is an increasing need for organizations to determine where their sensitive data is located, secure access to it and protect it accordingly. There are many products that incorporate the ability to Discover and Classify data. NC Protect is no different. However, what makes NC Protect unique is the ability to protect that data, no matter where it is located, instead of just reporting on it or attempting to move it to a quarantine folder. Read on to explore NC Protect’s capabilities for discovering and protecting sensitive data using existing classifications and metadata or NC Protect applied classifications.
Suppose you are already heavily invested in a Data Discovery and Classification solution. In that case, NC Protect can leverage existing classifications, metadata and Microsoft Purview Information Protection sensitivity labels to add additional access and security controls to the data. NC Protect specializes in protecting sensitive data and can apply a variety of mechanisms to do so on top of your existing or NC Protect-applied classifications.
Here are five practical use cases for NC Protect’s advanced capabilities for discovering and protecting sensitive data in your Microsoft 365 applications, SharePoint on-premises and file shares.
1. Protecting Sensitive Data through Obfuscation
NC Protect can obfuscate or hide sensitive files. Unauthorized users won’t be able to see that those files exist, even if those same users have full access to the Folder or Site Collection where the data resides.
For example, it can prevent the classic mistake of saving a sensitive file to a public directory, such as an HR file. NC Protect can apply simple rules to prevent anyone who isn’t part of the HR department and/or who doesn’t have ‘Manager’ or ‘Director’ in their title from seeing that particular file, even if it is accidentally placed in a public folder.
This is also a useful capability for controlling Guest Access. NC Protect can enforce rules to prevent Guest users from being able to see or interact with any type of sensitive data in your environment. This is a key concern for many companies when enabling Guest Access.
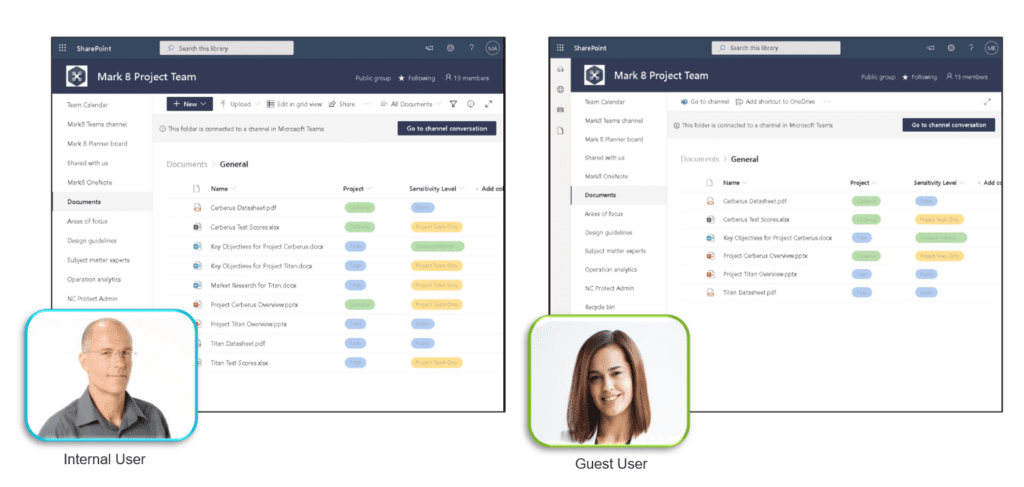
2. Redacting Sensitive Data
NC Protect also has the ability to redact or remove sensitive data from within a file. For example, maybe you want to give access to Customer Sales Order Forms to the shipping or customer service department. However, those order forms could contain sensitive information such as account or credit card numbers.
98% of the document is probably not sensitive and would be useful to both the Shipping and the Customer Service departments, particularly in cases where they need to verify an address, specific shipping instructions or similar information. However, you don’t want them to be able to view that credit card number if it’s in that document. Wouldn’t it be great if they could only view the portions of the document that aren’t sensitive?
NC Protect can redact the data you’ve deemed sensitive and leave the rest of the document accessible so the Shipping and Customer Teams can use it without revealing the sensitive information and potentially creating a compliance issue or data breach.
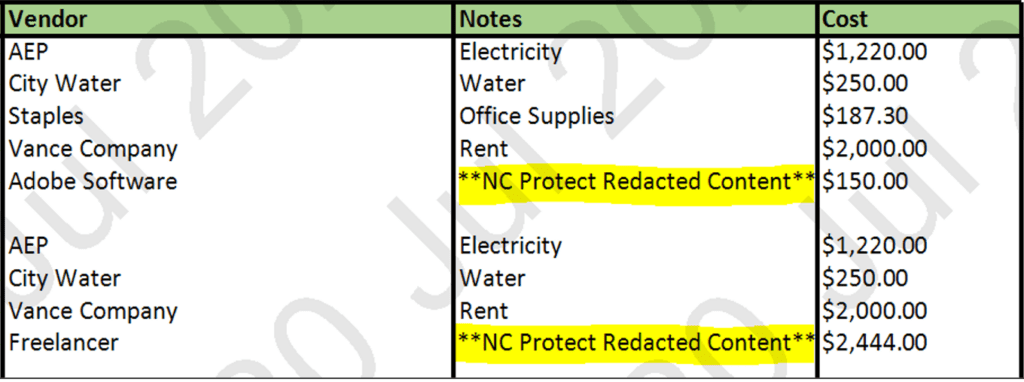
It can perform redaction while the data is in motion, so it’s not altering the source document in any way. It is only redacting the version that the end user can view. In this way, it can keep sensitive pieces of information out of the hands of people who shouldn’t see it while still allowing users who need access to see it to perform their job. This enables the secure collaboration of useful data between departments without creating separate documents or repositories.
3. Dynamic Security Watermarks
In addition to obfuscating files and redacting data, NC Protect can add dynamic security watermarks that contain any variables, such as the user’s name and the date, along with any other relevant data to make screen grabbing of sensitive data more challenging. This makes it much less likely that authorized users will leak sensitive data, such as company salaries, when their username and ID are splashed across a document.
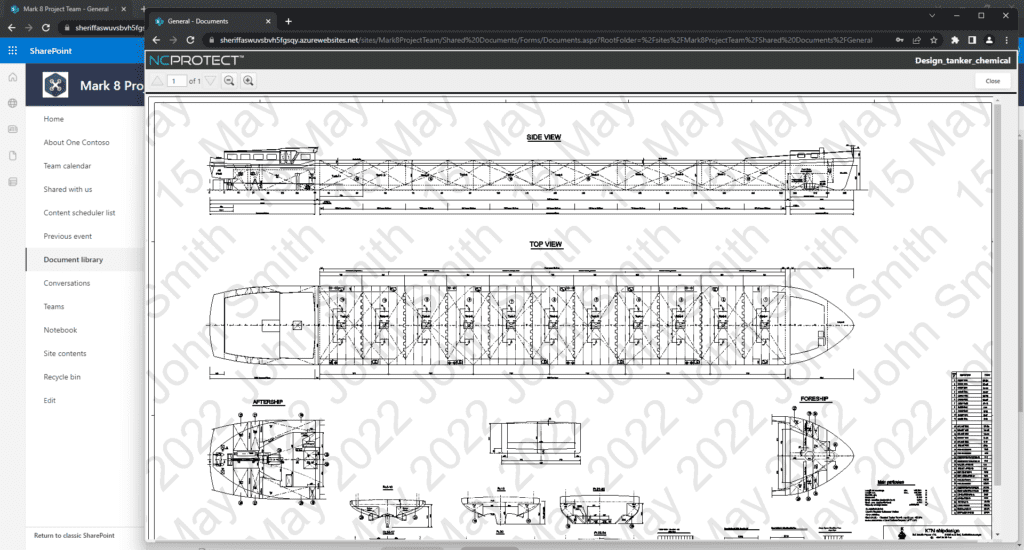
NC Protect’s data protection capabilities are far more flexible than just applying encryption to sensitive files. Encryption provides a lot of additional security to documents but can produce a lot of overhead. Many organizations want to take the extra step of encrypting sensitive documents but don’t want to deal with the hassle of encrypting all of their documents when they don’t need to. With NC Protect, only apply encryption if truly needed, not as a catchall for protecting sensitive data.
4. Discovering Sensitive Data
All this extra protection is excellent, but what if you don’t even know where your sensitive files are? NC Protect has its own Data Classification Engine and 200 out-of-the-box (OOTB) Rule sets for Accessibility, General Privacy, Financial Information, HIPAA data, CUI and more.
These can be used ‘as-is’ or customized to your organization’s specific needs. For example, I once had a client whose case numbers were in the following format: ###-##-####. Of course, this is the same format as US Social Security numbers. We were able to tailor the rule set to ignore Case numbers.
NC Protect’s OOTB rule sets are configurable to allow you to reduce the number of ‘false positives’ you receive and the number of ‘false negatives.’ For those not familiar with those terms, a false positive is a file that has been marked as sensitive that isn’t. A false negative is a file that is not tagged as sensitive, even though it is.
False positives can create a lot of additional overhead for managing files that aren’t actually sensitive (especially if you’re using a tool that is moving sensitive files to a quarantine folder). False negatives create overhead and risk potential as they can result in the loss of intellectual property, lack of confidence in the organization or even significant fines in the cases of HIPAA, PCI or GDPR failures.
5. Reporting on Sensitive Data Access
NC Protect can also produce reports to tell you where your sensitive data is located, who has access to it currently and who’s been accessing it. This allows you to provide tracking data to auditors, if necessary, as well as verify that the rules are working as intended. You can also easily ingest user activity and logs collected in NC Protect into Microsoft Sentinel via a free Connector or import it into Splunk to analyze the data at cloud scale and trigger holistic alerts and remediation actions alongside the dynamic and real-time access controls of NC Protect.
Taking a Proactive Security Posture
I always say that three types of people take security as a high priority.
- People who are forced to because of a compliance requirement.
- People who know that just about everyone will be breached eventually.
- People who have already been breached.
While finding and protecting sensitive data seems like an additional burden for many, the possibility of losing Intellectual Property, incurring significant fines, or just a huge hit to the bottom line can be a massive motivator to find and lock down data.
A large number of companies have had to provide credit check services to all users and undergone a significant loss of trust after a data breach. Unfortunately, not all of these organizations, especially smaller organizations, have been able to withstand these losses. Fortunately, most organizations have realized that security and data protection are critical operating expenses and are constantly re-evaluating their security posture.
If you have any questions about how NC Protect assists with discovering and protecting sensitive data, please don’t hesitate to contact us.