Microsoft 365 provides a powerful document management and collaboration platform. However, with so many applications available in the platform to store and share information internally and with external parties, such as partners, contractors and vendors, ensuring proper access and data security can be a challenge. In this blog we examine how to ensure secure file sharing in Microsoft 365 applications.
Microsoft 365 File Sharing Explained
The Microsoft 365 platform, formerly called Office 365, includes three file sharing applications: SharePoint Online, OneDrive for Business and Microsoft Teams. It’s not to be confused with the Office 365 applications that are still a part of the platform, which you likely use on a daily basis, such as Word, Excel and PowerPoint. Microsoft 365 or M365, as it’s often abbreviated, file sharing applications include:
- SharePoint Online – A powerful web-based application used for collaboration and information exchange. It’s the cloud version of its on-premises counterpart SharePoint Server.
- OneDrive for Business – A cloud storage service that houses your personal files and is private unless you chose to share the files or folders with others.
- Microsoft Teams – A collaboration hub providing users with capabilities for video conferencing, one-to-one and group chat, and file sharing. As we detailed in a previous blog, under the covers Teams file sharing is powered by both SharePoint and OneDrive.
How are Files Shared in Microsoft 365 Applications?
In each M365 application file sharing is handled a bit differently. Before we dive into the specifics, it’s important to note the two groups of people or users that you can share information with – internal and external.
Internal users are people within your company or the same Microsoft Entra ID domain with non-guest permissions.
External users called ‘guests’ are people from outside of your company, such as customers, partners, vendors and contractors. This is what we mean when we refer to guest access or permissions.
Now that we’ve defined the audiences for sharing, let’s look at how files are actually shared with each of the M365 file sharing applications.
Sharing Files in SharePoint Online
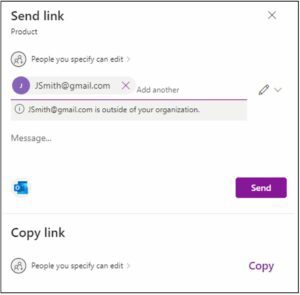
With SharePoint Online, as long as external sharing is enabled in your tenant, you can simply right click the file or folder that you want to share. You’ will be prompted for the type of people you want to share with (Anyone, specific people, people with existing access, etc.), and whether or not you want to allow editing or read only access. In the screenshot below, you can see that I selected, “Specific People” and left Editing enabled by default. In this case it’s an address outside of the organization so I get an informational notice below the email address. Then SharePoint will automatically send a sharing email to the selected user.
Sharing Files in OneDrive
OneDrive is a personal file storage tool that allows you to easily share OneDrive files or folders with anyone. Sharing is quick and easy. Just as in SharePoint (and indeed OneDrive can be considered a part of SharePoint) you simply need to select the file or folder you want to share, click the share button, and then select if anyone with the link can access it or limit who you want to invite and enter their email addresses. You can also limit the type of access granted such as view only or edit rights, set expiration dates and passwords to view content. It allows you to share files with both internal users as well as guests outside of your company.
While it’s extremely easy to share files with OneDrive, it requires the user to set the security on the document to control access and usage rights – making it easy to overshare sensitive information over time
Sharing Files in Microsoft Teams
In Teams, as we mentioned earlier, file sharing is a collection of many different services that are brought together in a single view pane. Many are familiar with the Chat and Meeting functions, but there are several file sharing components behind those services.
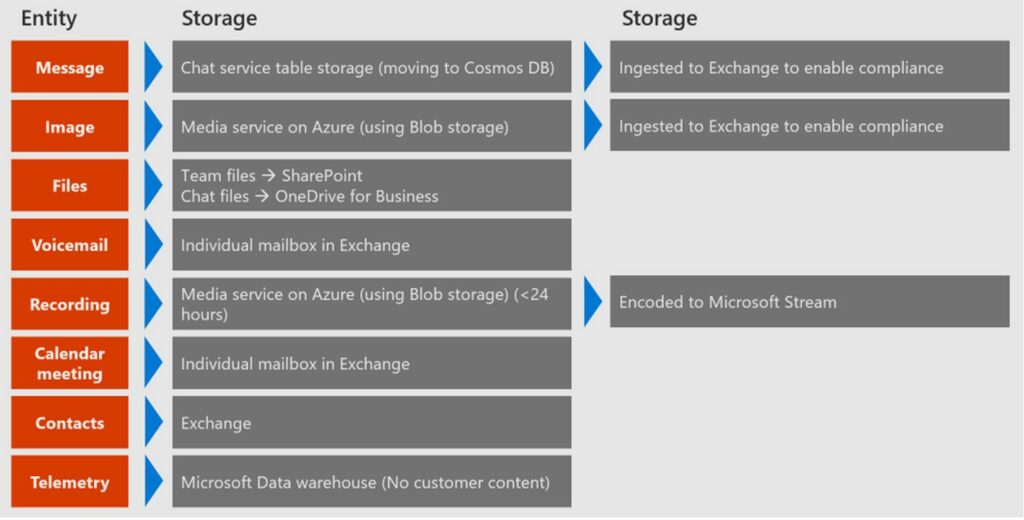
A typical Teams Channel (or group) uses M365 groups for permissions and security, SharePoint for file storage, Exchange for chat conversations and calendars, OneDrive for private file sharing. And then there are the Meeting, video-conferencing, voicemail, imaging and other underlying app services.
So, what happens when you create a Team?
- A new M365 group is created
- A new site collection and document library are created in SharePoint Online
- An Exchange Online shared mailbox and hidden calendar are created
- A OneNote notebook is made for storing whiteboard interactions
- Teams also creates ties into other 365 apps such as Planner and Power BI
When you create a Team from an existing group, that group’s members, its mailbox and notebook are surfaced in Teams. The diagram below illustrates how Teams makes use of Microsoft’s storage infrastructure to hold different types of data.
Beyond file sharing, Teams chat pose an additional security concern. You will likely want to control sharing of the information typed in chats in addition to file sharing. All of the same concerns with files sharing apply to chat content as well.
Challenges to Managing Information Security in M365
While all of these file sharing channels make it incredibly easy to share files with virtually anyone, they also open up huge risks for both accidental and malicious data loss.
Human error is and always will be a vulnerability and is the weakest link in any security strategy. Collectively referred to as insider threats, these stem from something as innocuous as sharing a sensitive file with the wrong user to someone with authorized access stealing the information for personal or financial gain.
Some examples of insider threats include:
- Employees who maliciously exfiltrate data when they are on furlough, gardening leave or have already been let go, using that data for personal gain, to sell or to gain trade secrets.
- Employees negligently exposing customer records. Experian South Africa exposed 250M customer records last year, to someone who was posing as a client.
- Employees who fall for phishing attacks. Think of how many of these users have clicked a PayPal or banking link to enter their information on a phishing website. And as a result, exposed their work and home passwords.
- Work-from-home employees who fall for ‘vishing’ attacks. Voice phising or ‘vishing’ is where someone may impersonate an IT administrator. Twitter employees were caught out by an attack in July 2020 and the fallout knocked 20% off of Twitter’s share price!
- Or, more commonly, sending an email to the wrong person. In 2015, a London HIV clinic sent a newsletter to 800 patients but left their names and emails visible in the TO field instead of Blind Copying them. That mistake cost the clinic hundreds of thousands of dollars in fines.
MICROSOFT 365 SECURE FILE SHARING BEST PRACTICES
In order to prevent accidental and malicious data loss M365 incorporates several capabilities and best practices to mitigate the risks that you should enable, including:
- Implementing Least Privileged Access to grant access only to the resources required by a user’s role.
- Utilizing Multifactor authentication, much more common these days, with a text message or authentication app on your phone.
- Limiting external sharing to Trusted Account – While policies and blocking email forwards are great in theory, they are horrible for productivity.
- Using Cloud App Security and Auditing to provide a detailed trail of who did what. Unfortunately, this is only possible after a breach has already occurred.
In addition to these best practices, you should also consider adding dynamic file protection above and beyond what’s native inside of M365 today to handle different file sharing scenarios consistently.
In the diagram below, an organization is using Microsoft 365 for file sharing using SharePoint Online, OneDrive for Business and Teams. Both internal and external users are accessing these applications from different locations, including home offices and a coffee shop. They have different roles and therefore, different needs. There also may be different policies that should be applied to these users based not only on their locations but their device, OS, etc. If we take a look at who is accessing these documents, we can see one document that resides in the cloud that both a manager and an external developer, maybe a consultant, have access to. When each of these individuals is accessing the document, their different security will need to be applied to these items.
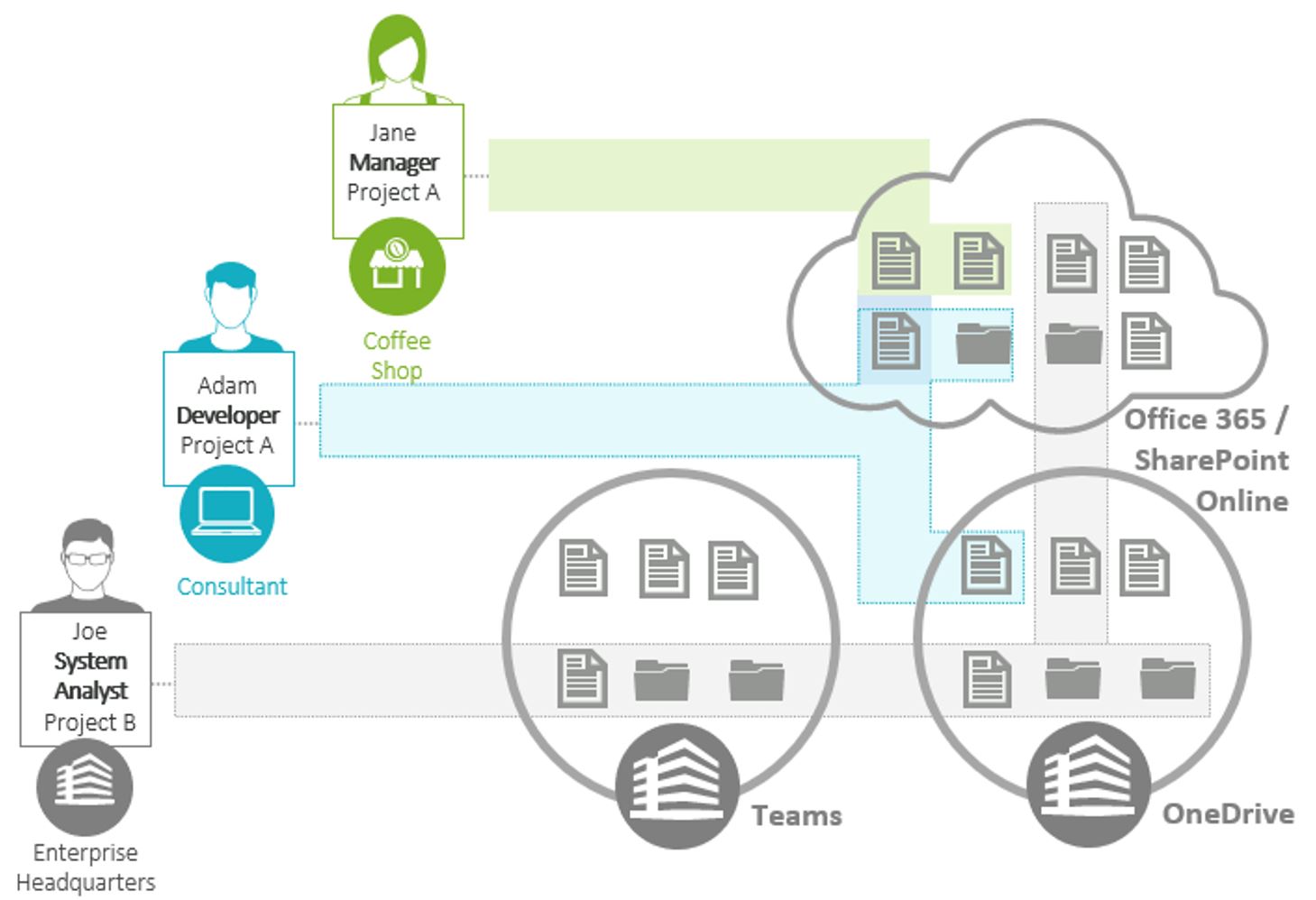
This example, in a nutshell, shows exactly how complicated it is to protect data in these different applications being accessed by internal and external users with different roles from different locations. A one size fits all static security policy simply is no longer viable. Instead, you need to consider the context of the access request (who is requesting access and under what conditions: time, location, device, etc.) and the sensitivity level of the data at the time of access in order to apply the most appropriate and effective security.
Dynamically Secure File Sharing in Microsoft 365
This is where a third party solution like NC Protect can enhance your native M365 security to adjust data access and protection controls in real time by considering the context of both the user and the file in real-time to apply dynamic protection. This approach to securing file sharing in Microsoft 365 applications provides far greater protection over insider threats.
Furthermore, NC Protect’s access and protection policies can be applied across M365 apps, including SharePoint Online, Office and Exchange.
If you’re struggling with this issue, contact us to see how NC Protect can secure file sharing in Microsoft 365 with simple-to-use, fast-to-deploy, dynamic data protection that won’t hinder collaboration.


