What is the NIST SP 800-162 ABAC Guide?
NIST SP 800-162 ‘Guide to Attribute Based Access Control (ABAC) Definition and Considerations’ is a special publication that defines attribute-based access control (ABAC) for U.S. government agencies. It also provides guidance on using ABAC to improve and maintain control of information sharing within and between organizations and best practices for ABAC implementations.
NIST defines ABAC as a logical access control model that evaluates rules against the attributes of entities (subject and object), operations, and the environment relevant to a request to grant or deny access. ABAC enables more precise access control with flexible policies that can accommodate multiple attribute combinations that are only limited by the available attributes.
Furthermore, with ABAC, access decisions can change between requests if attribute values are altered. This allows governance and security teams to create policies that dynamically adjust access, usage and sharing rights based on real-time comparison of user context and file content to enforce policies and enhance data protection.
ABAC allows enterprises to enforce the zero trust principles of ‘never trust, always verify’ effectively at the data access layer.
How Do ABAC Policies Work?
Policies form the backbone of ABAC. A policy is a rule that defines what actions (operations) may be performed upon the data (object), by whom (subject), and in what context the user may perform those operations (e.g., discover, read, create, edit, delete, and execute objects).
At a technical level, the ABAC Access Control Mechanism (ABAC ACM), also commonly called a Policy Engine, receives the subject’s access request and then examines the subject’s and object’s attributes against a specific policy. The ACM then determines what operations the subject may perform upon the object. If the combination of attributes satisfies the access control policy, then the user is granted access to the data and allowed to perform the desired operation(s). If the policy is not satisfied, then access is denied.
Below is an example of a simple ABAC policy: “If User A has Citizenship = United States, Clearance = ITAR Cleared, and Department = 1, access is granted.”
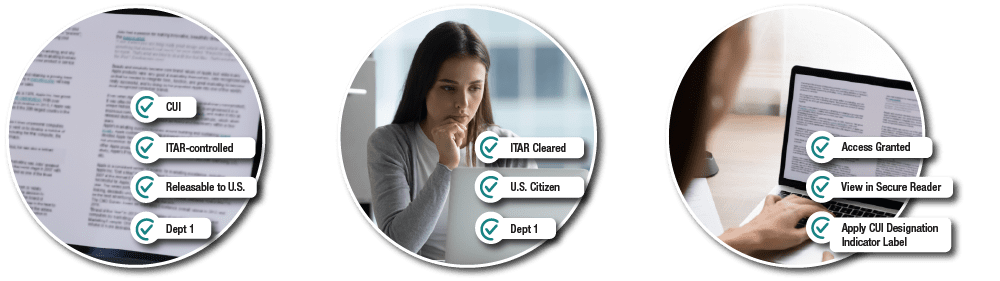
The attributes of sensitivity level, citizenship and department are applied to the document (object) manually or using automated tools.
User (subject) attributes are based on department, citizenship and ITAR clearance levels assigned to the individual.
If all of the conditions within the ABAC policy are met, access to the document is approved.
On a more technical level, the Access Control Mechanism (ACM) consists of various functional “points” that manage and retrieve policies. It also includes logical components that handle the context or workflow of policy and attribute retrieval and assessment. The four main functional points of an ACM include the Policy Enforcement Point (PEP), the Policy Decision Point (PDP), the Policy Information Point (PIP), and the Policy Administration Point (PAP). These components work together to make access control decisions and enforce policies.
An ABAC Access Control Mechanism for Microsoft Applications
It’s clear from NIST SP 800-162 that ABAC offers multiple benefits for improving access management. It is also an important component for executing a zero trust security strategy. ABAC policies can ensure that only the right people can access the right information at the right time with granular precision. This is why the complete portfolio of archTIS solutions leverages the ABAC methodology to ensure the highest levels of data access and protection.
NC Protect provides capabilities for easily adding ABAC to Microsoft 365, SharePoint on-premises, and File Shares. It’s a complementary product that Microsoft Security has recognized as a Privacy & Compliance Trailblazer Finalist. It allows enterprises to easily add ABAC to their existing Microsoft environment to dynamically control data access, usage, and sharing.
NC Protect’s dynamic policies offer more than just access control. They can also provide file-level protection, such as encryption, secure-read-only access, user-based watermarks, and more. Policies can also control with whom information can be shared, all in real time, using dynamic attribute-based access control and data protection policies. These policies automatically adapt to changes in user context and content changes, meaning that a user’s access and usage rights can alter depending on their location at any given time or if the sensitivity of the data changes. The product also includes a scanning and classification tool to aid in attribute management.
Implement Zero Trust ABAC-enabled Data Security with NC Protect
If you are considering the ABAC approach outlined in NIST SP 800-162, consider NC Protect from archTIS.
With NC Protect, sensitive content can be safely and confidently stored, shared, and collaborated on in Microsoft document management and collaboration platforms, using real-time ABAC and DLP policies. An ABAC-enabled approach also helps to control the proliferation of sites needed to support individual and geography-based collaboration scenarios using alternative access control methods.
Let archTIS assist your enterprise with implementing a Zero Trust ABAC-enabled approach that is simple to use, fast to implement and provides dynamic protection.
Solution Brief: NIST 800-162 ABAC Model
Explore how NC Protect implements Attribute-Based Access Control (ABAC) capabilities in line with NIST SP 800-162 to enhance your Microsoft security framework.


