Resource Center
Filter by
All Resources | Kojensi Resources | NC Protect Resources
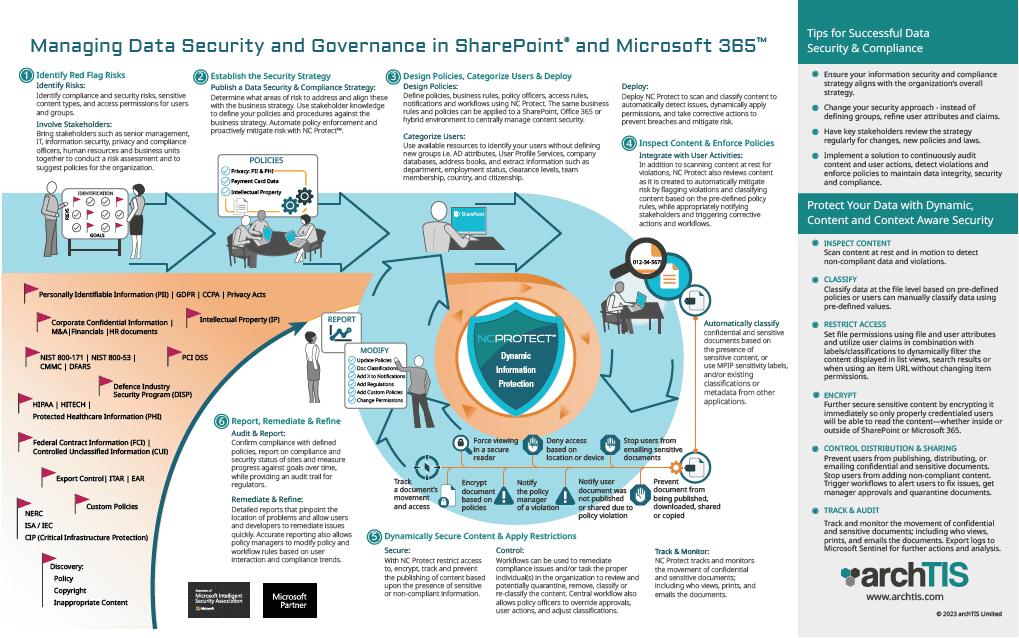
Infographic: Managing Data Security and Governance in Microsoft 365 & SharePoint
Get the steps for effectively manage data security and governance; from defining your strategy to using NC Protect to enforce compliance and apply dynamic security to Microsoft 365, SharePoint Server and file share content.

Webinar: Protect Sensitive Data with Microsoft Purview Information Protection & ABAC Policies
archTIS’ Dave Matthews and special guest Microsoft's Director, Director, Compliance and Privacy Ecosystem, Hammad Rajjoub, discuss how to enhance information protection controls to guard your most vital assets and ensure they don’t accidentally or deliberately walk out the door.

Datasheet: Kojensi for Government
Explore how Kojensi provides a faster, more efficient process for Government to securely share and collaborate on sensitive or Protected information internally and with partners.

Datasheet: Kojensi for Multinational Coalitions
Learn how Kojensi empowers Multinational coalition partners to share and collaborate on highly classified information with different security models on a single platform.

Datasheet: Kojensi for University Defence Research
Learn how to enable secure collaboration of sensitive and classified research between Universities, Government, Defence and Industry partners with Kojensi.

Datasheet: Kojensi for Critical Infrastructure
Discover how the Kojensi platform provides a cost-effective accredited platform to ensure the security of sensitive information for Critical Infrastructure to meet SOCI, SLACIP, and SoNS compliance requirements.

Datasheet: Kojensi for Intelligence Communities
Discover how Kojensi enables local, national and global intelligence communities to easily and securely share and collaborate on highly classified information in real time.

NC Encrypt Thales CipherTrust Manager Connector
The NC Encrypt CipherTrust Manager Connector provides an intuitive interface that links directly to CipherTrust Manager, enabling you to leverage your existing CipherTrust Manager keys to encrypt Microsoft application content.

Kojensi: Military-grade Sensitive & Classified Information Sharing Platform
See Kojensi's powerful ABAC powered policies in action in this platform capabilities overview video.

Case Study: SAP Secures Sensitive Government and Regulated Industry Data with Kojensi
Learn how Kojensi uses attribute-based access control (ABAC) policies to ensure both internal users across SAP entities, their customers and other third parties only have access to information on a ‘need to know’ basis.
Webinar: Independent Encryption Key Management and BYOK Support for M365 & SharePoint
Data encryption and key management are a core part of any organization’s security and compliance toolbox. However, many organizations prefer to manage their own encryption keys. In this recorded Webinar we discuss how to add independent key management and BYOK to your Microsoft 365 and SharePoint on-premises environments to minimize unnecessary access and build confidence in Microsoft services.

Request-For-Proposal (RFP) Template for Information Security Providers
Preparing a request for proposal or 'RFP' to purchase an information security solution to enhance data protection in SharePoint, M365, or Teams? Download this free RFP Template to easily collect important information and compare offerings from security software vendors to assist in the selection process.

Video: NC Protect Integration with Microsoft Purview Information Protection
Learn how Microsoft Information Protection sensitivity labels combined with NC Protect’s dynamic access and secure collaboration rules give you expanded protection and control over all your M365 collaboration.

White Paper: RBAC or ABAC? Adopting a Modern Zero Trust Approach to Data Access
This white paper explores the differences between Role Based Access Control (RBAC) and Attribute Based Access Control (ABAC) and their ability to support a modern zero trust approach to data access.
FCW CMMC 2.0 Workshop Brief
The U.S. Department of Defense has doubled down on how it protects CUI, underscoring the importance of using a solution that ensures any sensitive data is properly safeguarded. Read this handout to see how to protect DOD controlled unclassified information (CUI) from getting into the wrong hands.

Video: Applying CUI Markings with NC Protect in M365 & GCC High
Discover how NC Protect makes it easy to dynamically or manually apply CUI markings including CUI Designation Indicator label including Owner Name, Controlled By, Category, Distribution/Limited Dissemination Control and POC, as well as header/footer information into documents as a watermark.

Datasheet: NC Protect Advanced Watermarking
Learn about NC Protect's built-in Digital Security Watermarks to prevent data loss and aid in forensics. Advanced capabilities include the ability to apply CUI markings for CMMC, ITAR and NIST.
White Paper: Securing Multinational Coalition Collaboration with Data-Centric Security
Learn about the advantages of dynamic ABAC secured information sharing for Multinational coalition collaboration in Mission Partner Environments (MPE).
