Resource Center
Filter by
All Resources | Kojensi Resources | NC Protect Resources
Industry Report eBook: Optimize M365 for Controlled Content Services
Microsoft 365 enterprise presence is becoming ubiquitous. According to AIIM research, 93% of organizations ...

Brochure: NC Protect for Government & Defense
Empower your agency or Defense Industry Base (DIB) organization to take advantage of all the productivity and collaboration the Microsoft suite has to offer with meeting regulations including NIST, CMMC and ITAR for information security.

Case Study: NC Protect Seamlessly Manages CUI in SharePoint at this Defense Supply Chain Manufacturer
Learn how this Defense manufacturer uses NC Protect to identify and restrict access to Controlled Unclassified Information (CUI) in their SharePoint on-premises environment for ITAR compliance.

Data Sheet: NC Protect for SharePoint Server On-Premises
NC Protect provides advanced data-centric security for SharePoint Server 2010, 2013, 2016 and 2019 on-premises deployments, delivering enhanced information protection for on-premises environments that can be extended to hybrid and cloud M365 deployments should you migrate in the future.
Demo: NC Protect Automates Classification & Compliance
See how NC Protect’s dynamic classification and protection capabilities ensure compliance and secure sharing.

Demo: NC Protect for M365 and SharePoint
See NC Protect’s dynamic and unique data protection features to ensure secure collaboration, sharing and info barriers across M365 apps.
Webinar: POPI Act Compliance 7 Best Practices to Protect Personal Data
Amid growing risk, the need to comply with the Protection of Personal Information Act (POPIA), and the emergence of a remote and hybrid workforce, organizations must find ways to achieve a balance between enabling collaboration and securing sensitive information. You will discover the seven best practices for compliance with privacy legislation, without sacrificing collaboration.

Webinar: Stop the Top 10 Data Loss Scenarios
Since the onset of COVID-19, companies are reporting sharp increases in data loss spurred by remote and hybrid work. But, just how is all this data leaking with all the security measures enterprises have in place? View this webinar and explore our solutions to the different data loss scenarios that plague most companies.

White Paper: Building Dynamic Information Barriers in Microsoft 365
This white paper examines the challenge of building information barriers using role based security and how to create more usable separation for more complex use cases using dynamic attribute-based access control (ABAC) policies.

Data Sheet: NC Protect Data Connector for Microsoft Sentinel
Microsoft Sentinel is a cloud-native SIEM that you can use for intelligent security analytics across your entire enterprise. The NC Protect Data Connector for Microsoft Sentinel allows you to easily ingest user activity and protection logs and their associated “events” from NC Protect into Microsoft Sentinel.

Technology Brief: Meeting the US Presidential Executive Order for Zero Trust
The new U.S. Presidential Cybersecurity Executive Order for Zero Trust requires US Federal agencies to transition ...

Webinar: 5 Tips to Protect Your Sensitive Data in Nutanix Files
With remote work comes new risks and concerns about how data is accessed and used in cloud sharing apps like ...
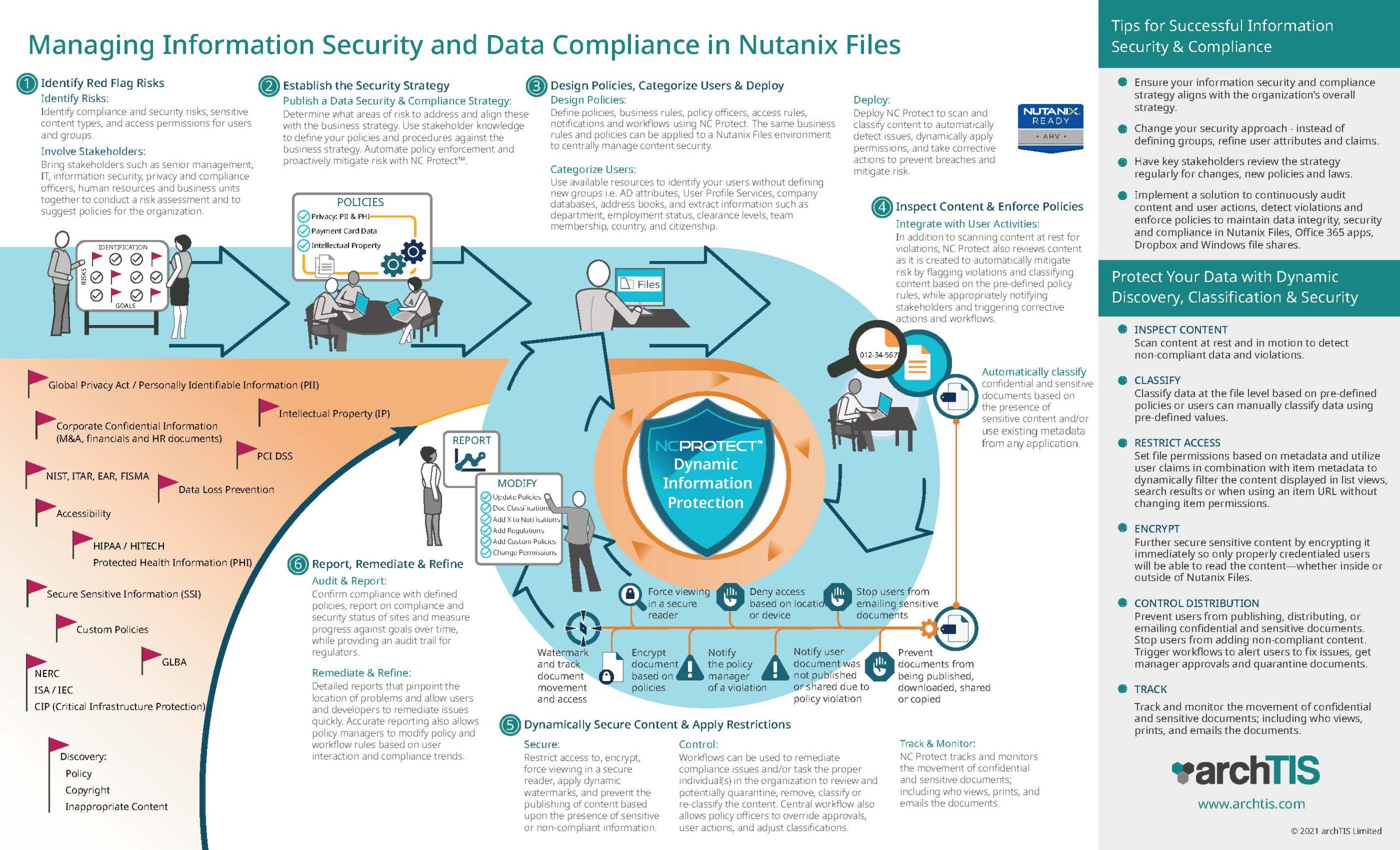
Infographic: Managing Information Security and Data Compliance in Nutanix Files
6 steps for effectively managing information security and compliance; from defining your strategy to using NC Protect to enforce compliance and apply dynamic security to data stored and shared in Nutanix Files

Webinar: Remote work is putting your data at risk. Protect it with Zero Trust.
The shift to remote work has organizations grappling with how to protect business-critical data. This Webinar ...

Webinar: Securing SharePoint Data as You Transition to the Cloud
This On-Demand webinar shares the challenges, best practices and most effective tools to migrating to a cloud ...

White Paper: Understanding and Meeting DISP Information Security Requirements
Understanding the complexities of DISP can be daunting. This white paper helps outline information and cyber security requirements and provides strategies to quickly increase compliance and cyber resiliency.

Data Sheet: Kojensi for DISP Information Security Compliance
Governance is critical to DISP accreditation, however, enforcing these guidelines is another matter. Built into ...

Case Study: Architecting the Single Information Environment Security Architecture (SIESA)
Learn about the award-winning Security Architecture for the Australian Department of Defence (Defence) Single Information Environment Security Architecture (SIESA).
