Protecting military secrets is critical to national security. It’s not just about securing information; it’s about ensuring our safety and maintaining a strategic advantage. Sweeping legislation, technology, and security protocols are in place to prevent classified information leaks within Defense, which extend down to Defense contractors. However, despite technological advances, humans remain the weakest link when it comes to protecting national secrets. In the latest incident revealed in an indictment this March, three US soldiers were arrested for involvement in a bribery scheme related to selling classified military information to China.
The allegations involve the unauthorized transfer of sensitive information, which includes documents concerning army combat vehicles, missile-related data, details about US Indo-Pacific military exercises, and 20 government hard drives, all passed to contacts in China as recently as December 2024. The alleged perpetrators include two active-duty US soldiers from Washington State stationed at Joint Base Lewis-McChord and a former soldier residing in Oregon.
Furthermore, video evidence from one of the military bases has emerged, showing one of the defendants using his smartphone to take photographs of his computer screen. This further supports the accusations against him and highlights how easily security measures can be bypassed with a mobile phone.
How prevalent is the human or insider threat to classified information?
The recent leak of classified information has brought to light a significant concern within the security industry known as “insider threats.” These threats emerge from individuals who may unknowingly compromise sensitive information through careless actions, as well as from those with malicious intent who may exploit confidential data for personal or financial gain. In some cases, these individuals may act on behalf of a third party or adversary, further complicating the issue, as demonstrated by this recent breach.
The prevalence and consequences of insider threats are alarming. Research conducted by Microsoft indicates that a staggering 63% of data breach incidents can be traced back to either inadvertent actions taken by well-meaning employees or deliberate actions by malicious insiders. This statistic underscores the critical need for organizations to implement robust security measures to mitigate the risks posed by both accidental and intentional breaches.
What can be done to prevent classified information leaks?
Ensuring the security of classified information requires a comprehensive approach. It is essential to implement multiple layers of both physical and technological security measures. A layered strategy is crucial for effectively preventing and deterring even the most persistent threats, as highlighted by recent security breaches.
- Implement Zero Trust – Zero trust has become the tech mantra of governments across the world to help thwart attacks from bad actors on the outside and within the walls of our institutions. The principle of zero trust is simple: verify anyone trying to connect to any systems, applications, or individual data files before granting access to them, each and every time.
- Enforce Physical Security – Physical premise security is a multi-layered process from the front door right through to the server room. Ensure government protocols for physical security are enforced.
- Robust Network security – Implement firewalls, enforce strong passwords, regularly update software, practice network segmentation, implement zero trust principles, use encryption, and monitor suspicious activity.
- Implement strong access control – Grant users only the necessary access to perform their jobs, ‘least privileged access,’ to minimize potential damage from compromised accounts. Implement fine-grained controls using methodologies like attribute-based access control (ABAC) to implement least privileged and zero trust principles effectively at the data level.
- Utilize Dynamic Watermarks – Watermarks that are dynamically applied and include information about the document handler can help augment your information security practices. They provide a visual deterrent and aid in identifying the source of a data leak if a photo is taken.
Dynamic Watermarks Provide a Last Line of Defense
As the breach at Joint Base Lewis-McChord has shown, perpetrators will go through great lengths to get the information they want. Dynamic watermarks are the last line of defense when someone circumvents security with the click of a phone. They serve as a visual deterrent and act as a digital thumbprint that stays with the document if classified data is photographed, helping clearly identify a perpetrator and provide physical evidence of their crime.
archTIS products, including NC Protect and Kojensi, automate the watermarking of Office documents (Word, PowerPoint and Office), PDFs, CAD files, images and more, with details of the user accessing the file, including name, date, time, and any other attributes a company needs to track the chain of custody and warn users of document sensitivity.
While a single watermark is useful, applying a separate watermark to sensitive images in a document or presentation provides additional protection for those images. archTIS dynamic watermarking can individually watermark images and other elements within the document. This multi-watermark approach ensures that sensitive or copyrighted images are automatically marked as sensitive, offering an extra layer of security.
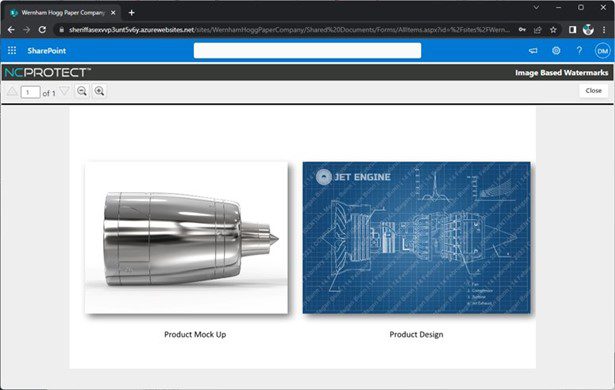
Watermark the entire document or individual images within a document with archTIS dynamic watermarks.
ABAC Policies Offer Adaptive Security
archTIS utilizes ABAC (Attribute-Based Access Control) to automatically apply policies based on a combination of user attributes, document sensitivity, and environmental conditions at the time of access. As a result, security controls and access rights can vary depending on the user and conditions.
For example as shown in the image below, the policy may allow a document owner to access and edit the document in an Office application, with no watermark. In contrast, if a guest user accesses the document, it will only be available in a secure, read-only Reader application, with the guest’s information digitally imprinted as a watermark.

archTIS Dynamic Watermark Advantages
While other security solutions may offer dynamic watermarking, archTIS provides the most comprehensive solution with the following key differentiators:
- Ability to set dynamic watermarks based on custom ABAC-defined policies, not a one-size-fits-all policy across your files.
- Watermarks can be applied to a wide range of file types, including Word, Excel, PowerPoint, PDF, CAD, text files and images.
- Any attribute can be used in a watermark: Name, email, date, time of access, IP address, file sensitivity level, etc. Watermarks are fully customizable.
- The entire document or individual images within the document can be watermarked.
- Ability to edit a watermarked file. Watermarks can be applied to Word, Excel, and PowerPoint files as they are edited, but cannot be removed by the user.
- Optionally, force users to view watermarked files in the Secure Reader app to prevent save as, print, copy, paste and download functions.
- Supports Controlled Unclassified Information (CUI) visual markings, including headers, footers and CUI Designation Indicator labels.
For more information or a demonstration of archTIS’ dynamic watermarking capabilities, contact us.


